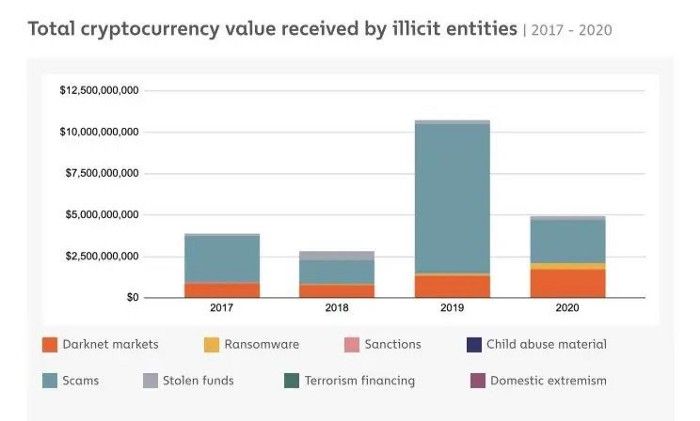
According to the Chainalysis Crypto Crime 2021 Report, criminal entities accounted for about 1% of the entire cryptocurrency activity in 2020. According to the research, crypto scams accounted for the majority of the actions these illicit monies were involved in. Ransomware and stolen funds accounted for a smaller fraction of the total, with darknet markets accounting for a significant fraction.
When scammers employ a fake identity, or any other malicious means, to take their cryptocurrency during what users perceive to be a genuine transaction, they’re engaging in a crypto scam. This type of scam can also entail the theft of their data and bank account information.
Another recent scam is when fraudsters imitating Elon Musk posted fake prizes online after his Saturday Night Live performance on May 8th, 2021. With the promise of a more significant return, some cryptocurrency investors were lured to move assets to unknown accounts. The reported losses total more than $2 million, despite earlier predictions of up to $5 million.
How do crypto scams work?
Step 1: The scammer attempts to join a well-known cryptocurrency community
Cryptocurrency groups exist to facilitate networking, knowledge sharing, and currency exchange. Members of a group are acquainted with one another and share personal information to develop trust, communicate, and trade cash. A fraudster will seek to join a group under a bogus identity, usually using social media means.
Step 2: The scammer tries to acquire cryptocurrencies.
Once a fraudster has gained the trust of a cryptocurrency group, they contact a member and offer to acquire cryptocurrency. The fraudster requests the member’s account information, a copy of their ID, an email address, and any other pertinent information to complete the transaction.
Step 3: The scammer shares forged documents.
The fraudster next submits what appears to be proof of a legal online banking payment relating to the bitcoin transaction after specifying the amount they wish to purchase. Some fraudsters may even submit what looks to be a copy of his or her overseas bank account statement.
Step 4: Fraudsters attempt trickery to gain access to cryptocurrency.
Cryptocurrency trading platforms advise sellers not to release cryptocurrency until they have received funds from the buyer. The seller will usually inform the fraudster that the funds have not yet been received.
Step 5: During the transaction, the scammer takes personal information.
A user may be vulnerable to subsequent compromises if he/she has provided banking information and personal details with a scammer during the transaction. The fraudster may then use his/her stolen identity to join a new cryptocurrency community and engage in other bitcoin scams.
Best practices to avoid crypto scams
- Being aware of the most frequent crypto scams
When a user first starts in the crypto world, they will almost certainly come across three different sorts of scams. Before becoming a victim and perhaps losing the assets, it’s critical to learn how to recognize these frauds. Let’s know about these three types of crypto scams:
- False cryptocurrency giveaways — Crypto giveaway scams are internet posts, mainly on social media, that ask users to deposit cryptocurrency to an address in exchange to guarantee that the sender will earn double or more in return. This type of crypto scam has been present since the 2017 initial coin offering (ICO) craze, and it follows a fairly strict formula. Fake cryptocurrency giveaway scams are easy to recognize if one knows what to look for.
- Scams via trading bots — Another common crypto scam is fake trading bot websites. These are platforms that guarantee users monthly returns that are extraordinarily high. These websites function like a Ponzi scheme, in which new money invested in the scam is utilized to pay out existing investors.
- Phishing attacks — Phishing attacks are getting more difficult to spot as fraudsters take more outstanding care in crafting emails that appear to come from respectable firms. Many will persuade users to click on links that infect the device with malware, granting the attacker complete access to the data saved on it.
2. Make no digital copies of personal crypto information.
Making digital copies of their crypto wallet passwords, seed words, or backup codes is one of the most common blunders made by new and seasoned crypto users. Users face the danger of a hacker acquiring access to their sensitive information as soon as they generate a digital copy of it through malware, brute force attacks, and other attack vectors.
3. When possible, always use two-factor authentication.
If two-factor authentication (2FA) is offered on the platform, it’s vital to enable it while creating a new crypto account. To give access to an account, 2FA is essentially a verification method requiring two or more pieces of information, usually from two different devices.
While there are a few alternative ways to achieve this, such as receiving an SMS or receiving a code via email, the great majority of crypto platforms require the user to download a third-party mobile app that connects to the new account and produces a random, self-destructing, six-digit password that is replenished every 30–40 seconds. Any service gains a crucial second layer of security as a result of this.
4. Use a unique password
Set two-factor authentication on all of your crypto accounts, copy all of the sensitive data on paper or metal plates, and be constantly on the lookout for potential crypto frauds. Remember that any one of the websites visited by you could mistakenly disclose your information, including email address and password. This should be avoided at any cost.
It’s critical to have different passwords for all of the crypto accounts to minimize the impact of data breaches and leaks on online security. Suppose a user has numerous accounts and can’t recall multiple passwords at once. In that case, there are several free password-managing browser extensions and apps that can store and generate secure passwords for user’s platforms.
To access the app and all of the password data saved inside, all the user has to do is create a master password. As the user goes on a platform, many password managers will automatically fill in any pre-saved login details and prompt to store any new login details to the vault when the user creates them. Along with these details, users should never voluntarily share seed phrases or OTP with anyone regardless of who it is, no matter what.
5. Selecting a safe exchange platform
A cryptocurrency exchange platform that wants to offer the best services would provide their users the safest experience and ensure to take all necessary safety measures to avoid crypto scams at any cost. So if one is looking for the best platform to put the best efforts into avoiding crypto scams, Giottus, a Chennai-based cryptocurrency platform, is the right choice. Giottus ensures that users have a safe trading experience by including features such as cold wallets protected by 100 percent insurance against cyber theft. Giottus has teamed with Bitgo, a world leader in custodial services, to ensure that our users’ investments are insured.
Conclusion
Those who think they might be a victim of a crypto scam should seek help right away. It’s crucial to remember, though, that pursuing legal action to recover monies placed into a fraud can be costly, and the blockchain research that’s sometimes required makes crypto scams even more complex.
Hopefully, this article has helped in understanding and bringing more awareness about crypto scams. Move to Giottus to have the best and safest cryptocurrency trading experience in the game. To know more, click here.
